If you're like me you struggle to create "good" passwords.
Sure, you can have Firefox generate random alphanumeric strings (with punctuation) for each login. But then you're locked to your home computer. You could create a "memorable" password by taking inspiration from around you. But I think most people are familiar with what happens when you try to recall an "easy" password like "BackstreetBoysPringles" a week or more later. "What was on my mind last week?", is the typical confusion experienced.
No, the solution to the problem is to have a fixed password making system, that you can rely on so you can retrace your steps in the future. The system should be robust. It should create high strength, yet memorizable passwords. And it should be more or less convenient, so that you're actually persuaded to use it rather than being lazy and using an improvised password every time.
To that end I think the most important thing you can do is be prepared. I'm not going to lie, if you need dozens and dozens of passwords then you're probably going to want to prepare the passwords ahead of time, and have them written down on a piece of paper (or other secure medium) for when you need them. However if you only need a few passwords per year, and you're at home when you need to make one, then this method will be fine for on the fly generation.
Let's start with a brief primer on computer security.
Computers are secured from other computers by computational complexity. Computers are very good at making guesses very quickly. They can exhaust an entire dictionary in seconds, which is why "password" really should mean "passphrase". You want a password with complexity.
The way we measure that complexity is with a number called "bits of entropy". With a numeric code of just the gylphs 0-9, you have less complexity, you have less combinations than you can have with both numbers and letters. A 6 digit password only has a million possible combinations, while an an lowercase and uppercase alphanumeric password has (10+26+26)^6 possible combinations. The difference is huge. But we can make a quick calculation of taking the log of 2 of those base numbers and we can say that each character has that many bits of entropy. Because 2 to the n power is the number of different possible combinations.
So a number character has 3.3 bits of entropy, a letter has 4.7, and a random character from the full set of 95 printable ASCII characters has 6.5 bits of entropy. But here's a nifty trick. If we just thrown in ONE symbol character in with regular letters, then a computer won't know where it is and will have to assume that ANY character is a symbol and will have to brute force the entire password as if any and all characters could be anything. So that's why it's important to have one of each in your password, because it's a simple way to add complexity. Pick a digit and a punctuation symbol (possibly the same set over and over again) and put that at the end of every bad password you've ever made, and suddenly your password is a lot better. It's not as good as if your password were perfectly distributed random characters from the entire printable ASCII set, but that's only better in theory. And besides, if you were to do that good luck remembering it.
So the question now becomes, "Well, how many bits of entropy do I need?". And the answer is "That depends.". Typically we have different strengths for different levels criticalness. And different attack vectors. My rule of thumb is, that you should have about 32 bits minimum for everything. That's for web stuff, like your social media, your AOL instant messenger account, what have you. Then for web services that you actually pay money for maybe 64 bits. And then your banking and work accounts should be around 96. And finally your encryption passwords should be 128 bits. And that's because the nature of encryption cracking. With web hacking, I believe that timeouts make network login attacks infeasible, so it's acceptable to have less entropy for those passwords. Encryption on the other hand needs more bits because they can brute force it offline much, much, faster.
A final note, since your email is typically a gateway to infiltrating other aspects of your digital life, it might be prudent to have a maximally safe password for that. So 96 bits. I'm just saying that your email might be more critical than you might be aware. There have been wire fraud scams where hackers use people's assumption about email being legit to commit fraud. All it took in one case was a guy sending an email, "Hey we have a new bank account number now, send the payment to this routing number instead."
So now that I've explained the basics of password strength, let me tell you my recommendation for what a basic good general purpose password would look like. I recommend an English word, followed by a punctuation symbol, followed by a digit, followed by a uppercase letter. So that way the whole range of characters are represented at least once. You have lowercase, uppercase, numbers, and punctuation symbols. And the English word is easy to remember. Perfect.
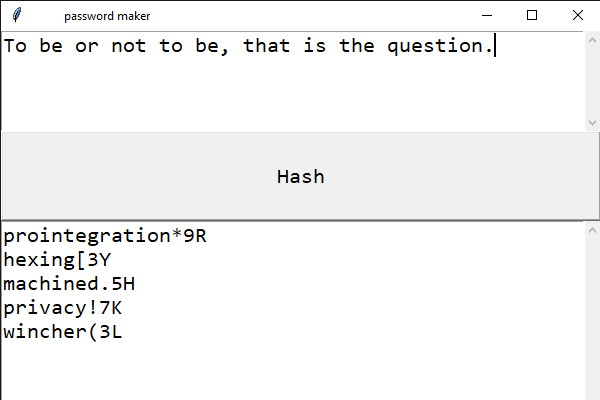
Here is an example: teacher%2G
If stronger password strength is needed, you can simply use two or more of these strung together.
So now that we know what we want the final product to look like, is there a way to have these be the product of a well defined, deterministic, and easy to recreate process? Of course. The word "deterministic" might be a clue to what I'm going to do next. Computers are very good at doing things "deterministically".
There is such a thing in computer science as a "hash algorithm". There are many to choose from in fact. If you've ever calculated file checksums to verify data integrity you know what I'm talking about. With a hash algorithm we can input any arbitrary length data input and get a complicated, hard to predict, pseudo random binary output.
Md5 checksums output a 128 checksum. But I'm gonna go ahead and use SHA-1 because it gives us a 160 bit output. So what we can do is have a LONG input seed, hash that, and then use the resulting 160 bit checksum as the basis for creating my recommended password type. I have given these passwords a name. I call it a wordcherry, because it's a human readable word, plus a cherry of extra hacker busting complexity on top. I have written an algorithm that when given a specific binary number, it deterministically creates a wordcherry from that number. Basically it's way to map bits to passwords that are memorizable. If we can use retrieveable seeds to create them, we can have a way to recreate the same exact password. It is a way to shrink a long password into a shorter more convenient one.
This allows us to grab a random book off a bookshelf, pick a random page, pick a random line, (or a memorable one) and input that into the password algorithm, and then have 5 good memorable passwords made from it. And we can throw away the passwords, and simply rely on the knowledge of where the particular passage in the book is to "remember" what our password is. All you have to do is make sure that your seed passage has sufficient bits of entropy so that computers don't just brute force your seed. About two sentences will do the trick. I think an English language word has about 6 or 7 bits of entropy.
That's it. That's my password making algorithm. Use books as entropy seeds from which to generate passwords. If you take the time to slowly read the context of the passage when you're creating the password, you will be able to find it again later. You can make an effort to if not memorize the seed verbatim, to remember the meaning, and push comes to shove, you can read the entire book again. You will recognize the passage. "Oh hey. That's my seed!" Locking yourself out of accounts should be a thing of the past.
If you're worried about other people reading this and hackers adapting to the algorithm and sidestepping the entropy somehow, you're free to modify any portion of my algorithm. You can put the name of your pet at the end of every seed. Or you can rotate the sequence of the wordcherry. Or you use jpg photographs instead of books. Though I do believe even the NSA and FBI would have a hard time brute forcing EVERY source of entropy on your bookshelf. Did I say two sentences? Maybe you want to do three and a half instead. I encourage you to modify my algorithm to suit your own needs.